Hacking Homes For Fun: Chapter 2 - The Alarm Tag
Nowadays most of the home alarms use a contactless tag to activate/deactivate the alarm. Those tags bring cryptographic functionalities; however, I want to verify if they are really used. As an example, the remote control of Chapter1 had anti-replay capabilities which were not used by the system integrator.
I started analyzing the type of tag of the home alarm, this can be easily done using an NFC enabled smartphone and the NXP Tag Info application. The tag is an ISO15693 with cryptographic capabilities.
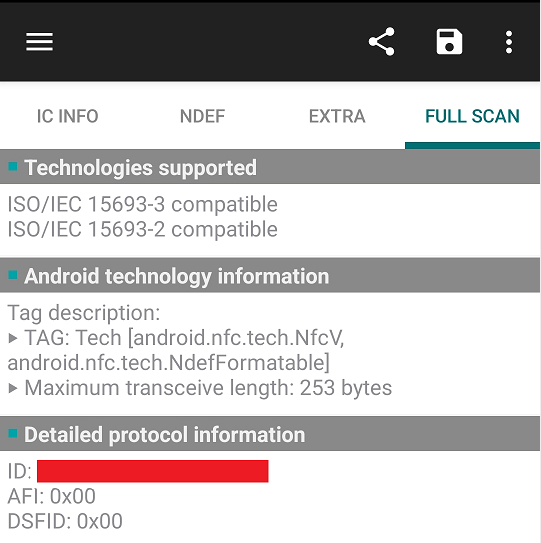
NXP Tag Info also indicated that no cryptographic keys were set, therefore, I suspected that the alarm device only checks the UID of the tag. The UID is a unique identifier which must NEVER be used for security means, as it can be easily replicated.
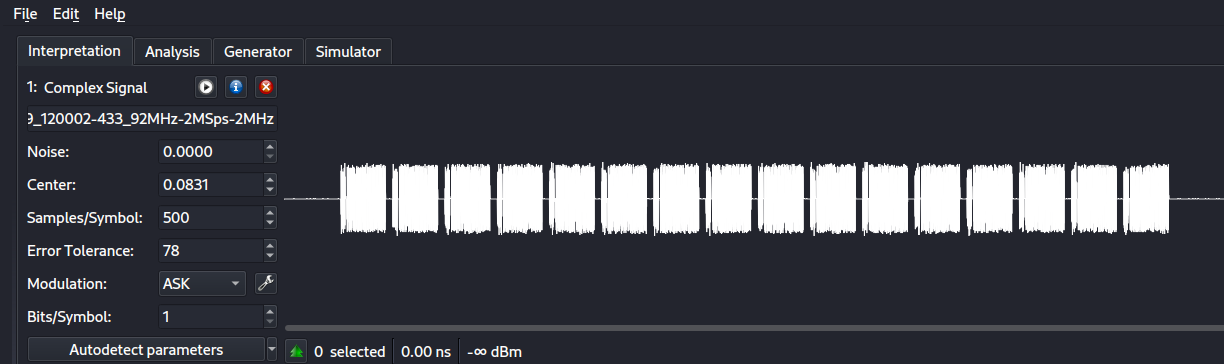
After the initial analysis, seems clear that it will not be very hard to create a fake tag to deactivate the alarm. To do so I used the Proxmark3 as shown below. Basically, I used a script to use the standalone mode which has two steps:
- Reader mode, reads a Tag which is approached.
- Emulation mode, emulates the read Tag.

Once the Tag was emulated, I performed a proof of concept to verify that the Alarm Tag could be bypassed, the steps to conduct were:
- Activate the alarm
- Once the alarm was activated, use the emulation tag to deactivate it.
The results can be seen below:

As in Chapter1, although the tag implements cryptographic functionalities, the system integrator chose not to use it, probably for simplicity or lack of security knowledge.
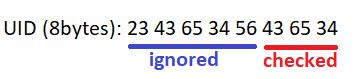
Even more; after further research I was able to identify that only the 3 last bytes of the UID were checked. The other 5 bytes were ignored:
I already advised both the alarm manufacturer and the system integrator, and they indicated that the security would be enhanced :).
Tema General Tema1 Tema2 Tema3 Tema4 Tema Spec 1 Tema Spec 2 Tema Spec 3 Tema Spec 4 Tema Spec 5 Tema Spec 6 Tema Spec 7 Tema Spec 8 Tema Spec 9 Tema Spec 10 Tema Spec 11 Tema Spec 12 Tema Spec 13 Tema Spec 14 Tema Spec 15 Tema Spec 16 Tema Spec 17 Tema Spec 18 Tema Spec 19 Tema Spec 20 Tema Spec 21